
A new RedLine malware distribution campaign promotes fake Binance NFT mystery box bots on YouTube to lure people into infecting themselves with the information-stealing malware from GitHub repositories.
Binance mystery boxes are sets of random non-fungible token (NFT) items that people buy, hoping they’ll receive a unique or rare item at a bargain price. Some of the NFTs found in these boxes can be used to add rare cosmetics or personas within online blockchain games.
Mystery boxes are trendy in the NFT market because they give people the joy of the unknown and the potential for a big payday if they land a rare NFT. However, marketplaces like Binance offer them in limited numbers, making some boxes hard to get before they run out of stock.
This is why interested buyers often deploy “bots” to acquire them, and it’s precisely this hot trend that the threat actors are trying to take advantage of.
YouTube and GitHub abuse
According to a new report by Netskope, threat actors are creating YouTube videos to entice potential victims into downloading and installing the malware on their computer, thinking they’re getting a free mystery box scalper bot.
.png)
BleepingComputer confirmed that the videos listed in the indicators of compromise are still available on YouTube, albeit having a low number of views.
There likely are many more than those spotted by Netskope, and it’s also possible that previous scam videos with a higher number of views were reported and taken down by YouTube moderators.
The threat actors uploaded the videos between March and April 2022, and they all feature a link to a GitHub repository that supposedly hosts the bot but, in reality, distributes RedLine.
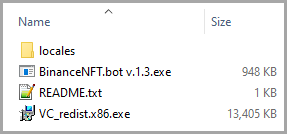
The name of the dropped file is “BinanceNFT.bot_v1.3.zip”, containing a similarly-named executable, which is the payload, a Visual C++ installer, and a README.txt file.
(Netskope)
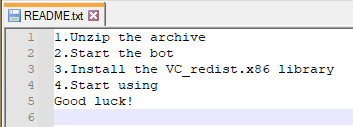
RedLine requires the VC redistributable installer to run since the program is developed in .NET, while the text file contains the installation instructions for the victim.
In this campaign, RedLine was configured to exit if the malware detected the country on the host computer to be Russia, Ukraine, Belarus, Armenia, Azerbaijan, Kazakhstan, Moldova, Uzbekistan, Tajikistan, or Kyrgystan.
In addition to the RedLine campaign seen by Netskope, BleepingComputer noticed newer YouTube campaigns promoting a free ‘Binance NFT Bot.’
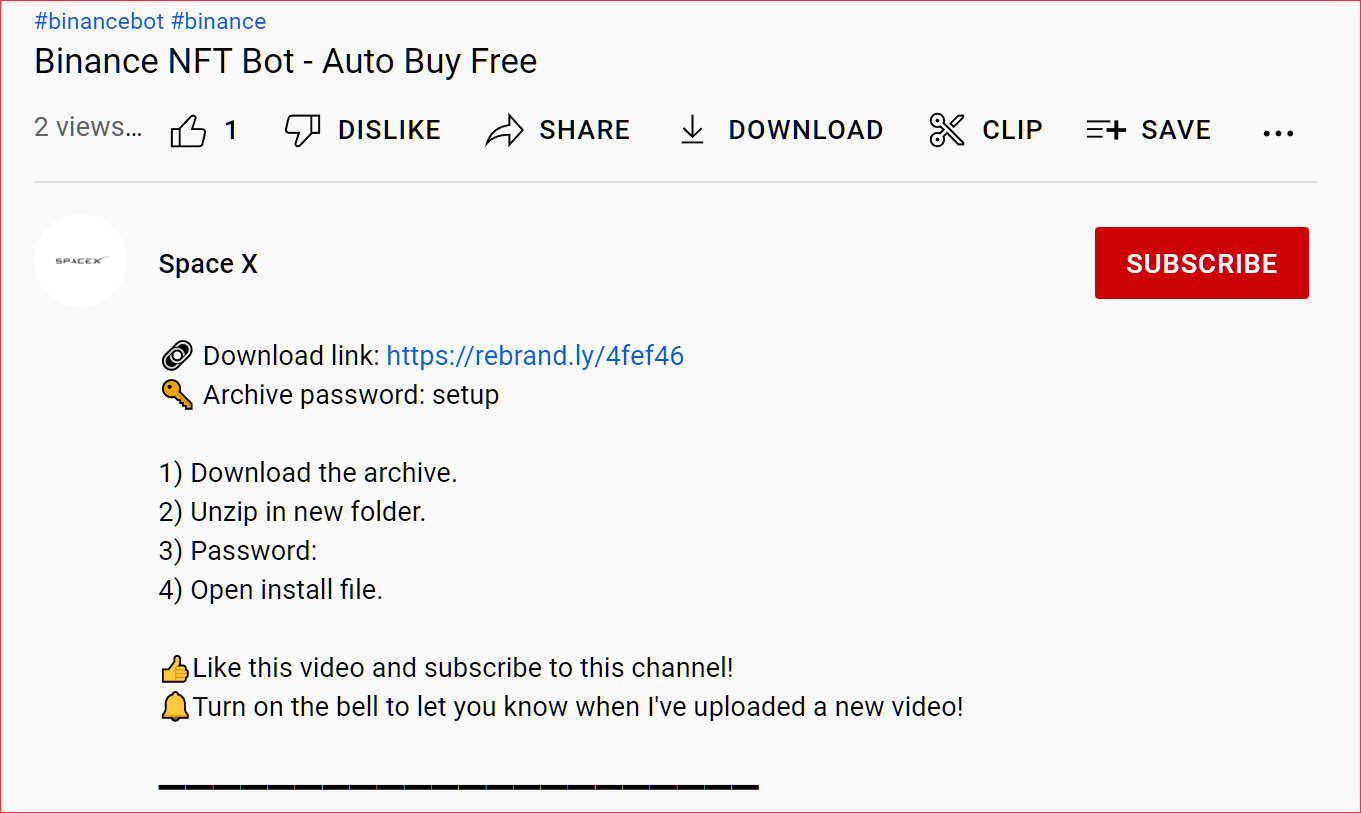
Source: BleepingComputer
However, these campaigns are using rebrand.ly URLs that redirect to downloads hosted on MediaFire. According to VirusTotal, this campaign is also distributing password-stealing trojans.
RedLine threat continues
RedLine is a very popular and potent threat in the information-stealing malware space, being distributed by multiple threat actors and in a wide variety of ways.
It’s currently sold to independent operators under a subscription model for $100 per month and supports the stealing of login passwords and cookies from web browsers, data from chat apps, VPN credentials, and cryptocurrency wallets.
In cryptocurrency-themed campaigns, such as this one, the victims typically possess digital assets and cryptocurrency, making the financial damage even more significant.
One thing to always keep in mind is that the legitimacy of platforms like YouTube and GitHub does not automatically equate to content trustworthiness, as the upload checks and the moderation procedures on these sites are lacking.
Clicking on links provided under or on videos uploaded by small and obscure YouTube channels, downloading executable files, and running them on your system is never a good idea.
This news is republished from another source. You can check the original article here.

Be the first to comment